Seems like I’m staying on track for a post every 18-24 months, so it’s time…
Some of us have to deal with NIST 800-53 controls. You certainly must if you’re in government or are government-adjacent. A few private organizations also use them. One of these, AC-8, has been implemented in Splunk over the years in a few different ways. One of the most common has been to use the login_content option in the [settings] section of web.conf. For folks required to use DISA STIG standards, there’s a prescribed approach that uses login_content in combination with an HTML <script> tag requiring users to acknowledge (press OK) before they can log in.
This satisfies paragraph (b) of the control statement:
Retain the notification message or banner on the screen until users acknowledge the usage conditions and take explicit actions to log on to or further access the system
There’s a problem though – at some point, Splunk started to “sanitize HTML for security purposes by removing potentially dangerous tags and attributes”, and <script> seems to be one of those.
So then, what can we do instead? The first time a user logs in to Splunk Cloud Platform, they’re presented with a EULA acceptance panel. Turns out, this is implemented using the termsOfServiceDirectory that is also available in standard Splunk Enterprise.
The way it works is with an app named tos and numbered HTML files. If the user has not accepted the highest numbered TOS file, they’ll be prompted to do so. Their acceptance is stored inside the tos app. Let’s give it a try!
splunk@fedora:~$ /opt/splunk/bin/splunk create app tos
App 'tos' is created.
splunk@fedora:~$ cd /opt/splunk/etc/apps/tos
splunk@fedora:~/etc/apps/tos$ mkdir local && cd local
splunk@fedora:~/etc/apps/tos/local$ cat <<EOF > web.conf
> [settings]
> termsOfServiceDirectory = /opt/splunk/etc/apps/tos/tos_html
> EOF
splunk@fedora:~/etc/apps/tos/local$ mkdir /opt/splunk/etc/apps/tos/tos_html
splunk@fedora:~/etc/apps/tos/local$ cat <<EOF > /opt/splunk/etc/apps/tos/tos_html/1.html
> <P> This is a usage notice </P>
> <P> It can say whatever you want it to </P>
> EOF
splunk@fedora:~/etc/apps/tos/local$ systemctl restart Splunkd.serviceNow, when I access my local Splunk I get one of these – but only on the first login.
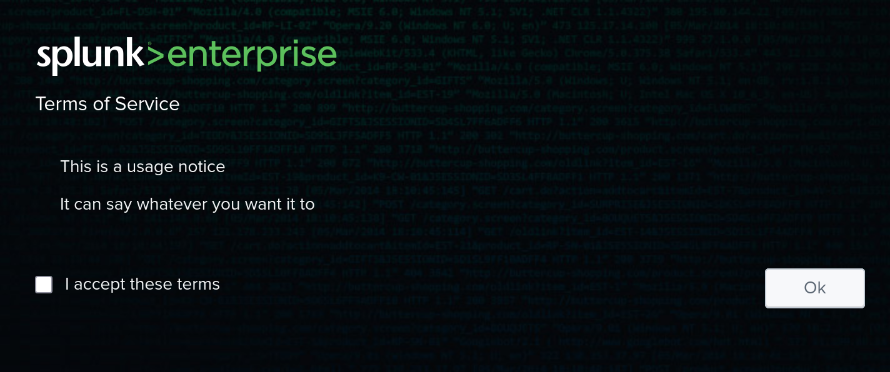
But, you know what? A numerical reference, with the highest integer taken? Sounds a bit like an epoch. We’re one small shell script and a cron job away from something neat.
splunk@fedora:~/etc/apps/tos/local$ cd /opt/splunk/etc/apps/tos/bin/
splunk@fedora:~/etc/apps/tos/bin$ cat <<'EOF' > update_tos.sh
#!/bin/bash
cd /opt/splunk/etc/apps/tos/tos_html
mv $( ls *.html | head -1 ) $( date +%s ).html
EOF
splunk@fedora:~/etc/apps/tos/bin$ chmod +x ./update_tos.sh Now we can add this to our cron scheduler like so:
splunk@fedora:~/etc/apps/tos/tos_html$ crontab -l
* * * * * /opt/splunk/etc/apps/tos/bin/update_tos.shNow, every minute we’ll move the one and only TOS file to a newer timestamp, requiring users to agree to it on each login. It’s a bit hacky but it works